What Characteristic Describes a Trojan Horse
The first one is its concealment. A network device that filters access and traffic coming into a network.
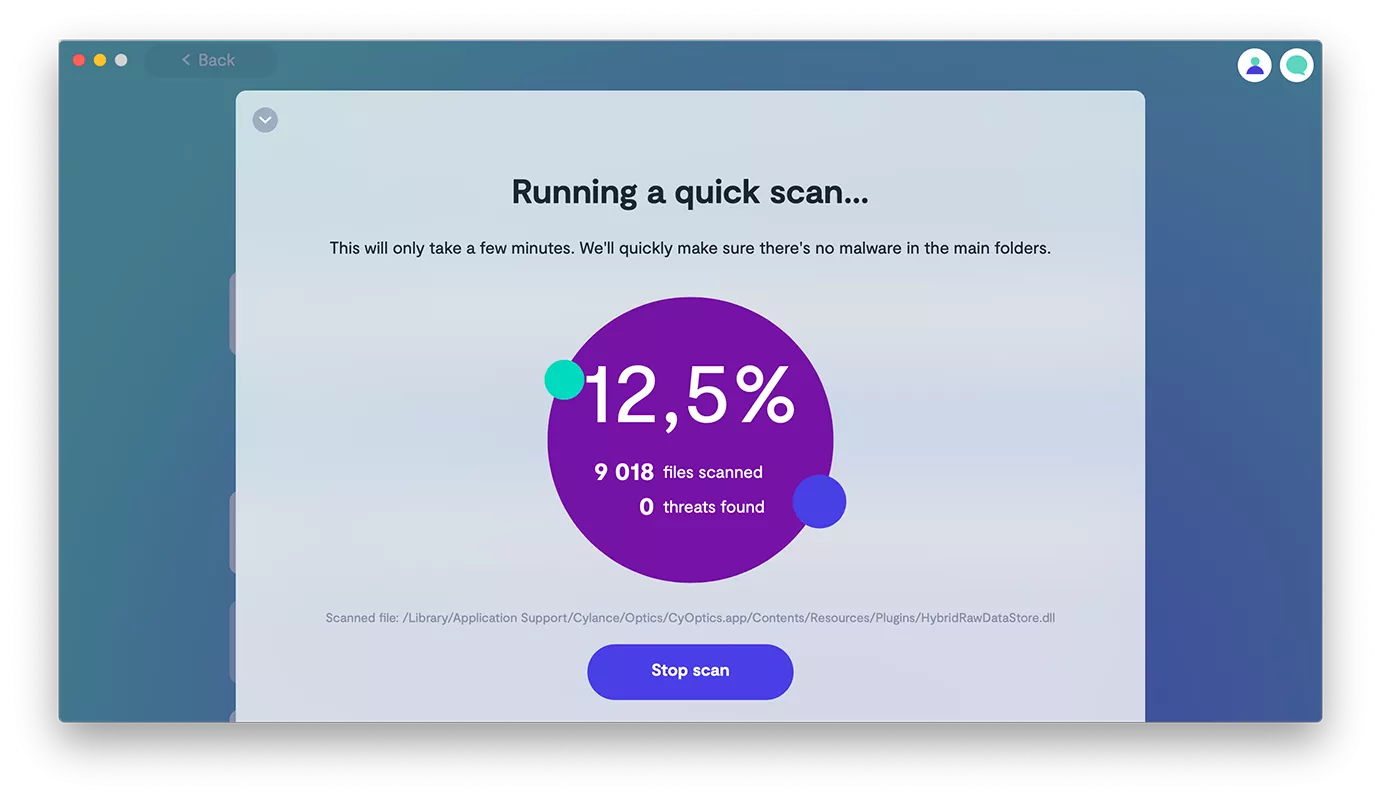
What Is A Trojan Virus Definition Types Prevention Tips
What characteristic describes a Trojan horse.
. A technician with a PC is using multiple applications while connected to the Internet. An attack that slows or crashes a device or network service. Trojan horses are malicious programs that look legitimate but can take control of your computer if they are installed on your computer.
A brute-force attack commonly involves trying to access a network device. An attack that slows or crashes a device or network service. A Trojan can be used to perform an action once it has been installed.
A denial of service DoS attack results in interruption of network services to users network devices or applications. What service is provided by HTTPS. Malicious software or code running on an end device.
On the opposite side the goal for Trojan is to arrive stole remote control. Extreme quantities of data are sent to a particular network device interface. Malicious software or code running on an end device.
What characteristic describes a Trojan horse. An attack that slows or crashes a device or network service. Uses encryption to secure the exchange of text graphic images sound and video on the web.
A network device that filters access and traffic coming into a network. Malicious software or code running on an end device. An attack that slows or crashes a device or network service malicious software or code running on an end device a network device that filters access and traffic coming into a network the use of.
Once installed a Trojan can. Malware is contained in a seemingly legitimate executable program. A computer that has unexpected changes to its settings and unusual activity even when it should be turned off is strongly suspected of being infected with a Trojan.
A network device that filters access and traffic coming into a network. It is designed to damage disrupt steal or in general inflict some other harmful action on your data or network. What is a characteristic of a Trojan horse as it relates to network security.
What characteristic describes a DoS attack. What characteristic describes a Trojan horse. An electronic dictionary is used to obtain a password to be used to infiltrate a key network device.
A network device that filters access and traffic coming into a. An attack that slows or crashes a device or network service. An attack that slows or crashes a device or network service.
Malicious software or code running on an end device. What characteristic describes a Trojan horse. Malicious software or code running on an end device.
A buffer overflow occurs when a program attempts. If the Trojan cannot be elusive it is meaningless. A network device that filters access and traffic coming into a network.
Malicious software or code running on an end device. In general a Trojan is designed to damage disrupt steal or in general cause some other harm to your data or network. CCNA 1 v70 Final Exam Answers.
Secondly Trojan has strong fraudulence. An attack that slows or crashes a device or network service malicious software or code running on an end device a network device that Continue Reading What characteristic describes a Trojan horse. A network device that filters access and traffic coming into a network.
What characteristic describes a Trojan horse. Trojan is similar to remote control IT Technical Services but remote control software like team viewer is friendly. A Trojan horse is software that does something harmful but is hidden in legitimate software code.
What characteristic describes a Trojan horse. Malicious software or code running on an end device. What characteristic describes a Trojan horse.
A Trojan horse is a malicious program that appears harmless on the surface but actually has malicious intent. What characteristic describes a Trojan horse. What characteristic describes a Trojan horse.
Trojan horse or Trojan is a type of malicious code or software that can take control of your computer. What characteristic describes a Trojan horse. The use of stolen credentials to access private data.
The use of stolen credentials to access private data. An attack that slows or crashes a device or network service. How is the PC able to keep track.
So it doesnt have concealment. An email pretending to represent a legitimate organization asking for personal information. About This Quiz Worksheet.
An attack that slows or crashes a device or network service. What are three characteristics of the CSMACD process. What Best Describes A Trojan.
Trojan horse viruses are very sneaky and the worksheetquiz pairing is written to see what you know about a Trojan horse. What characteristic describes phishing.

Ccna Cyber Ops Version 1 1 Chapter 6 Exam Answers Full

Ccna Cyber Ops Version 1 1 Chapter 6 Exam Answers Full

Quest For Beauty Nestor Achilles Neoclassical Painting

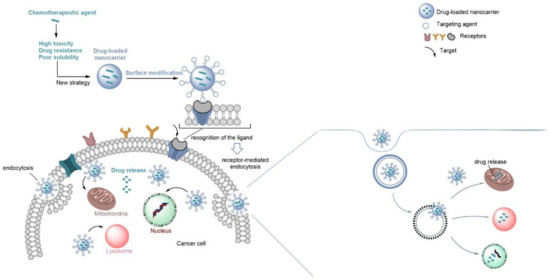
Biomedicines Free Full Text Functionalized Liposome And Albumin Based Systems As Carriers For Poorly Water Soluble Anticancer Drugs An Updated Review Html

7 Types Of Computer Malware And How To Prevent Them In 2022 Titanfile
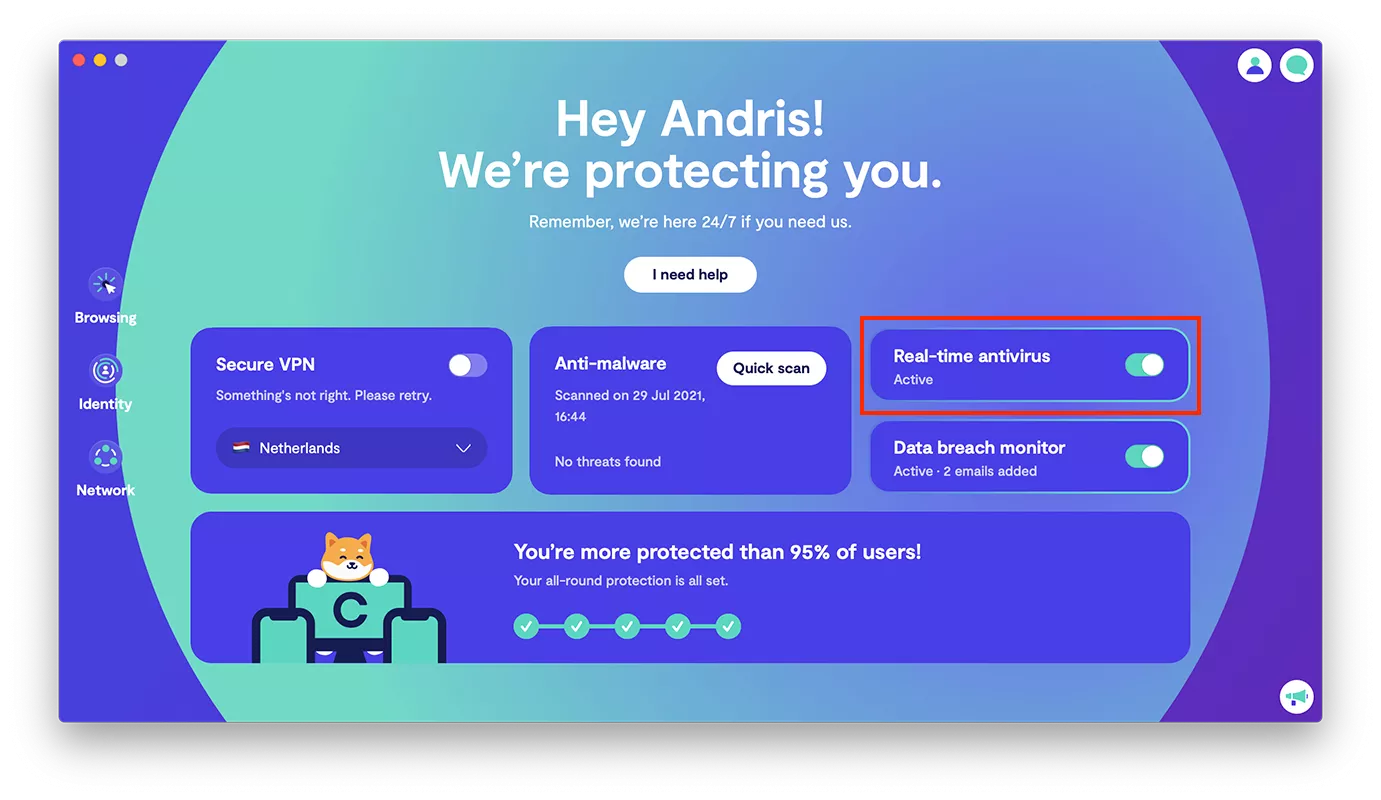
What Is A Trojan Virus Definition Types Prevention Tips

Trojan War Definition Summary Hero History

What Is A Trojan Virus Definition Types Prevention Tips

Colors Craft Decor Garden Garden Decor Videos Handmade Home Living Shopwallsteet Toy Wood Wood Cr Backyard Lighting Backyard Decor Rustic Backyard

Dunhill Rollagas Lighter Gold Plated Black Panel Lacquer Ultra Rare Excellent Condition Lighter Gold Black Panels

Ccna Cyber Ops Chapter 6 Exam Answers Version 1 1 2019 Full 100

Colors Craft Decor Garden Garden Decor Videos Handmade Home Living Shopwallsteet Toy Wood Wood Cr Backyard Lighting Backyard Decor Rustic Backyard

Ganymede Eagle Mosaic At Bignor Roman Villa This Impressive Mosaic Was The Centrepiece Of A Dining Room Or Triclinium Ancient Art Roman Art Roman Mosaic

Ccna Cyber Ops Version 1 1 Chapter 6 Exam Answers Full

Comments
Post a Comment